Research
- Privacy Preserving Data Analysis
- Construction and Security Analysis of Post-Quantum Cryptosystems
- Cryptanalysis
- Improvement of Block Chain and Application
- Privacy Preserving Technique without information manipulation
- Highly Dependable System Software
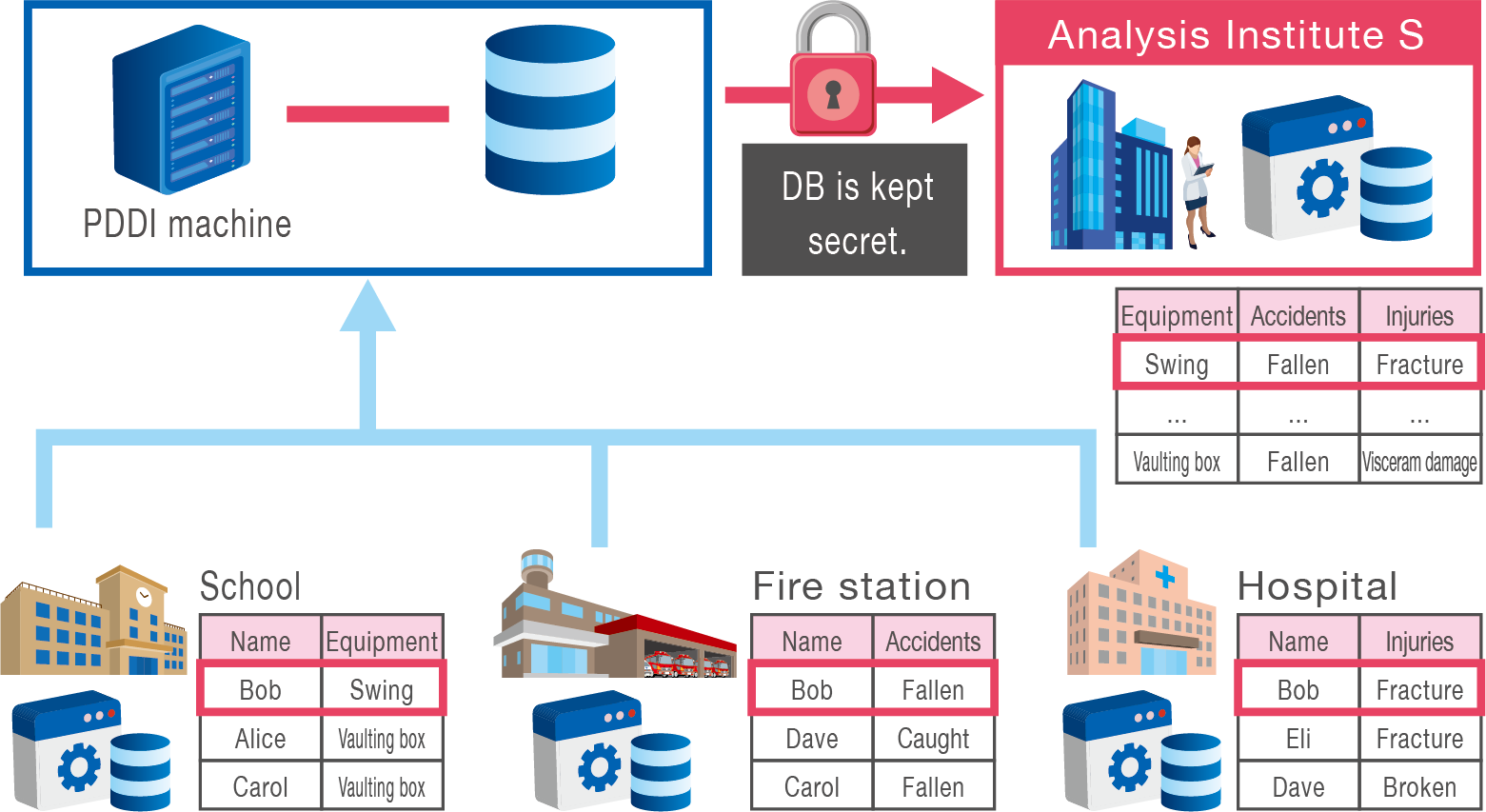
Privacy Preserving Data Analysis
Existing Problems
When a child is injured on a swing in an elementary school, the data on playground equipment where the accident occurred is managed by a school, the data on emergency transportation to the hospital is managed by a fire department, and the data on injury and sequelae is managed by the hospital.
Data on school-accidents is distributed at schools, fire departments, and hospitals.
A privacy-preserving method of integrating distributed data is essential for big data analysis.
Lab Research Target
We realize a privacy-preserving data integration system while distributing data to each institution without centralizing the data.
We also realize privacy-preserving integration of data contained in a certain number of institutions.
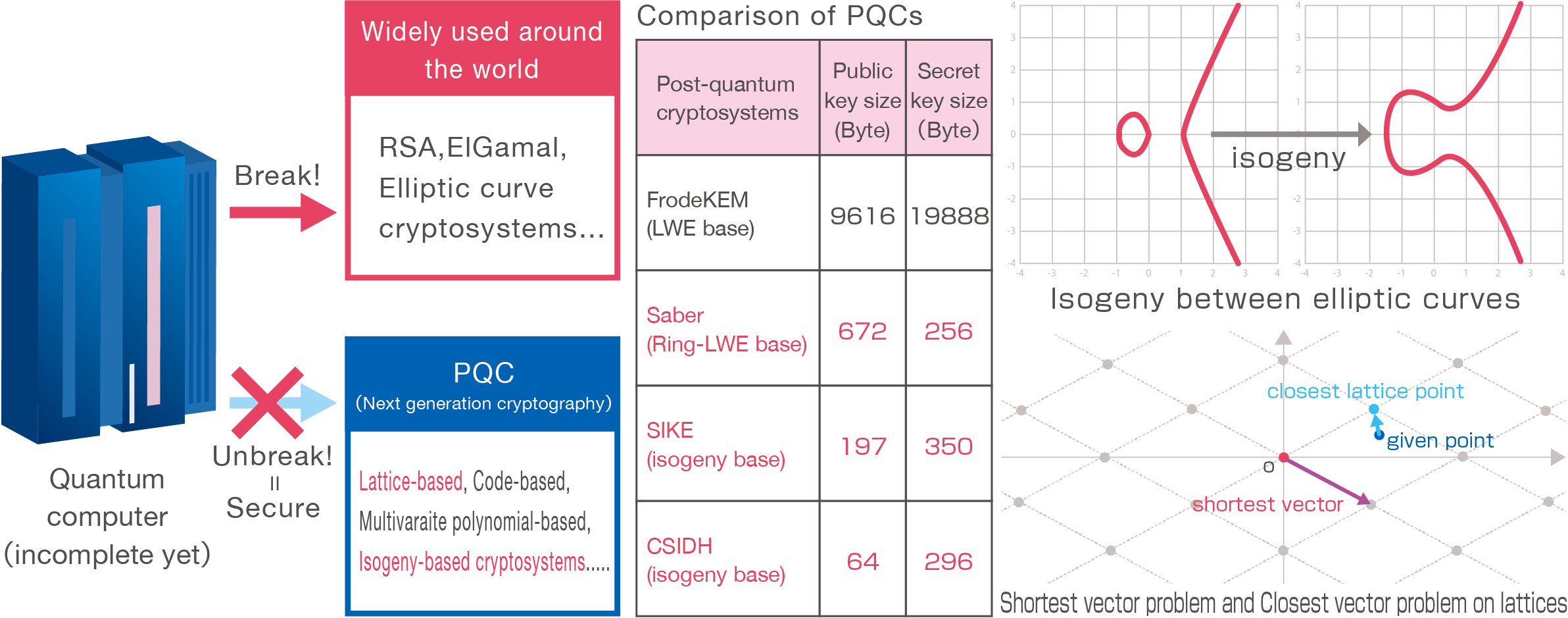
Construction and Security Analysis of Post-Quantum Cryptosystems
Existing Problems
In recent years, the development of quantum computers has been progressing, and it is said that a large-scale quantum computer will be completed between 2030 and 2040. Large-scale quantum computers can break RSA cryptography and elliptic curve cryptography, which are the basis of current public key cryptography.
Therefore, it is necessary to realize technologies such as key sharing and anonymous signature schemes, which are realized by non post-quantum cryptosystems, by post-quantum cryptosystems (PQC) which is secure against quantum computers. It is also necessary to improve the efficiency of performance of PQC such as processing speed, public key and ciphertext sizes and to analyze the security of PQC.
Lab Research Target
We research on lattice-based and isogeny-based cryptography as PQC, to construct PQC-based key sharing and anonymous signature schemes or to improve the efficiency of speed or memory, and to analyze security experimentally and theoretically.
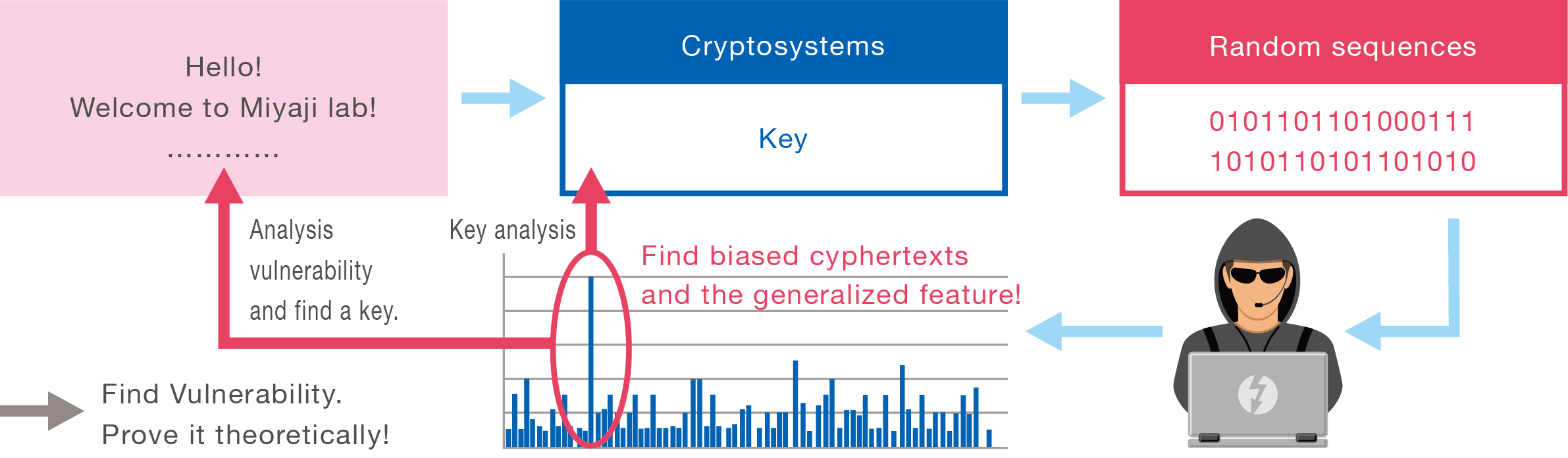
Cryptanalysis
Existing Problems
With the advent of the corona era, new communication such as online classes and online meetings using zoom has been added.
- Are people in online really friends? Is our data kept secret?
- Is our data kept secret?
Cryptography is the technology that enables secure communication.
Cryptanalysis is indispensable for guaranteeing the security of cryptosystem Each research institute is competing for finding the vulnerability of the current cryptosystems.
Lab Research Target
We are conducting security analysis on ChaCha used in TLS and Salsa, which is the prototype of it.
By analyzing the bias of these large numbers of ciphertexts and discovering new vulnerabilities, we will clarify the conditions for designing stronger ciphertexts.
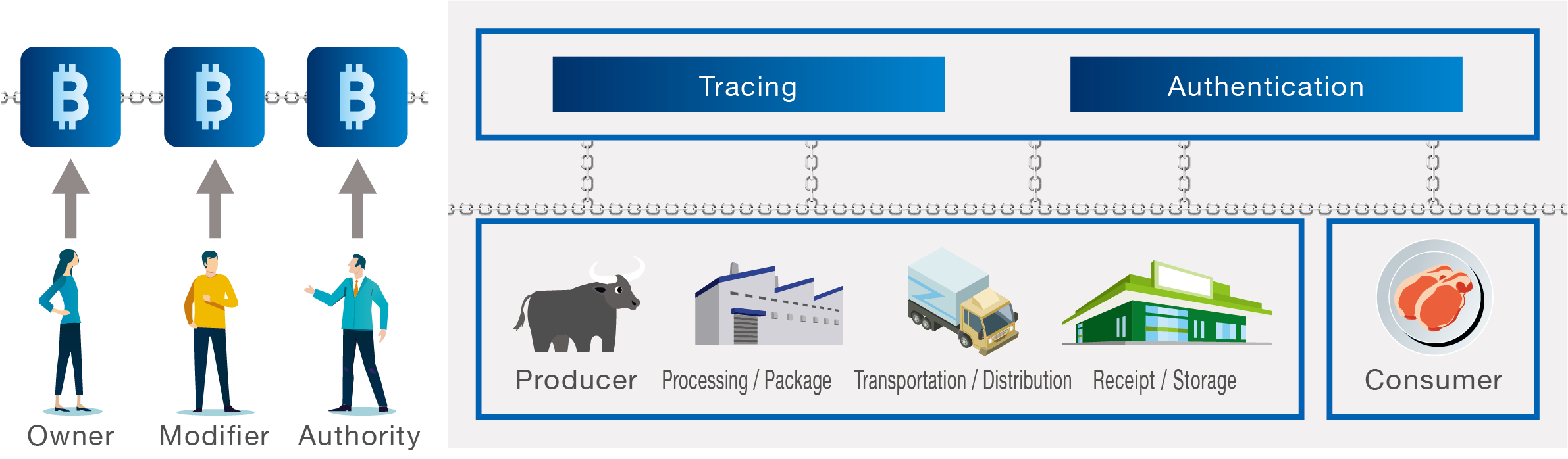
Improvement of Block Chain and Application
Existing Problems
Blockchain technology is not limited to a finance system such as Bitcoin but expected to achieve a trustworthy transaction system such as a food safety system using a supply chain, and an electric power traceability system on the deregulation of electric power.
It is also necessary to add new functions to the blockchain such as editable functions, and to assure the security to various attacks.
Lab Research Target
We construct various reliable digital systems using blockchains, realize blockchains that can be securely edited by constructing a Revocable Policy-based Chameleon Hash (RPC), and enhancing security against various attacks.
In this way, we will promote the digitalization using blockchain.
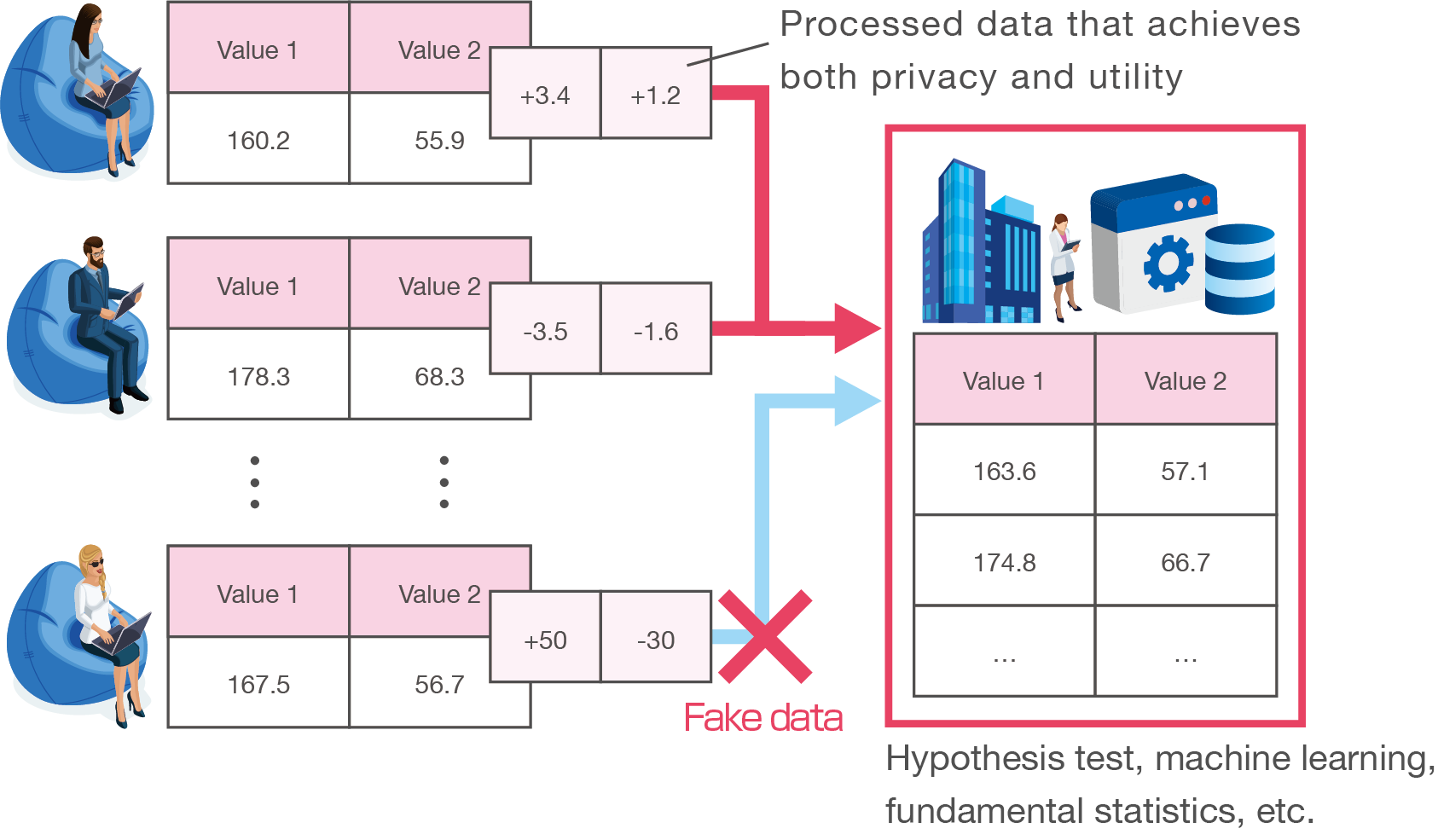
Privacy Preserving Technique without information manipulation
Existing Problems
Privacy-preserving methods for data utilization is a research for DX (Digital Transformation). Indices for data privacy and utility, and data processing techniques to achieve the indices have been proposed. However, introducing privacy-preserving techniques obscure the information of a data holder, and it is difficult to avoid information manipulation. Therefore, methods to avoid information manipulation while achieving privacy will become increasingly important.
Lab Research Target
We are studying data processing techniques that can maintain a balance between privacy and utility in each use case. We suppose malicious users, and our mechanism has a function to detect or avoid information manipulation from the malicious users.
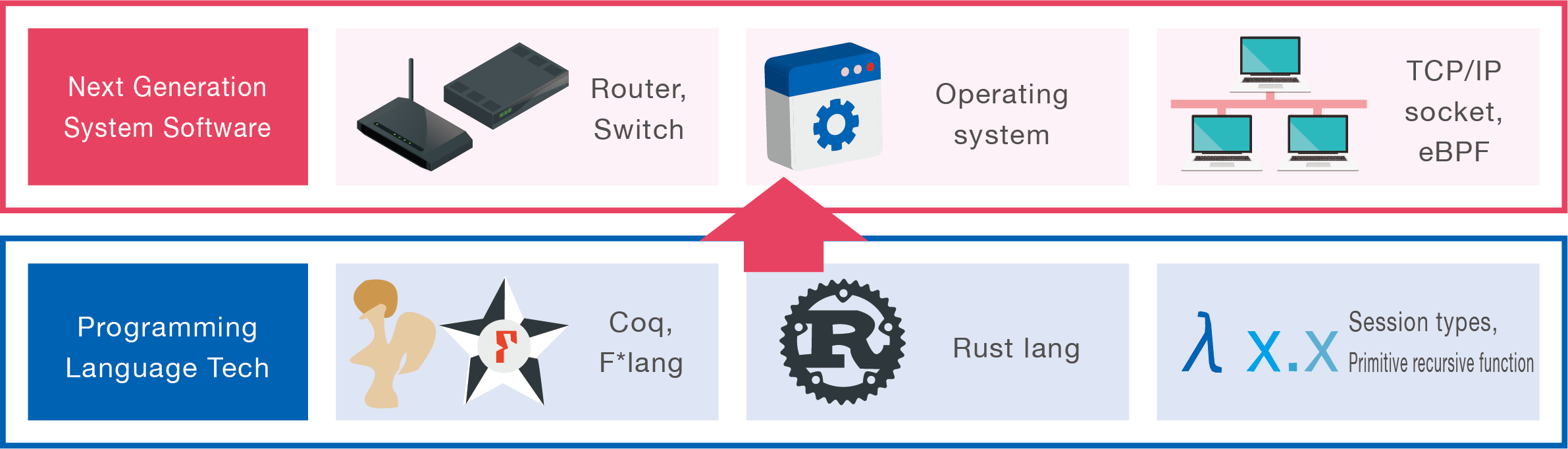
Highly Dependable System Software
Existing Problems
Because of IoT, embedded software and network software is sustaining our lives. However, there is still software vulnerability and it is a significant problem.
Software vulnerability will cause various problems such as system stopping, information leakages, system hijacking.
Lab Research Target
Our laboratory is studying next generation's design and implementation of system software, such as operating system and network software, by applying programming language technologies, such as Coq, F*, Rust, session types, primitive recursive function.